AUTHOR: ROSE Kelley
DATE : 02/03/2024
Cloud-based software has revolutionized the way businesses operate, offering scalability, flexibility, and cost-efficiency. In a country like India, where digital transformation is rapidly unfolding, the adoption of cloud technology is on the rise. However, with this adoption comes the challenge of managing high-risk cloud-based software effectively.
Understanding High-Risk Cloud-based Software
High-risk cloud-based software refers to applications and services hosted on cloud platforms that pose significant security and compliance concerns. These risks stem from various factors, including the sensitivity of the data being stored or processed, the vulnerabilities within the software itself, and the potential threats from malicious actors.
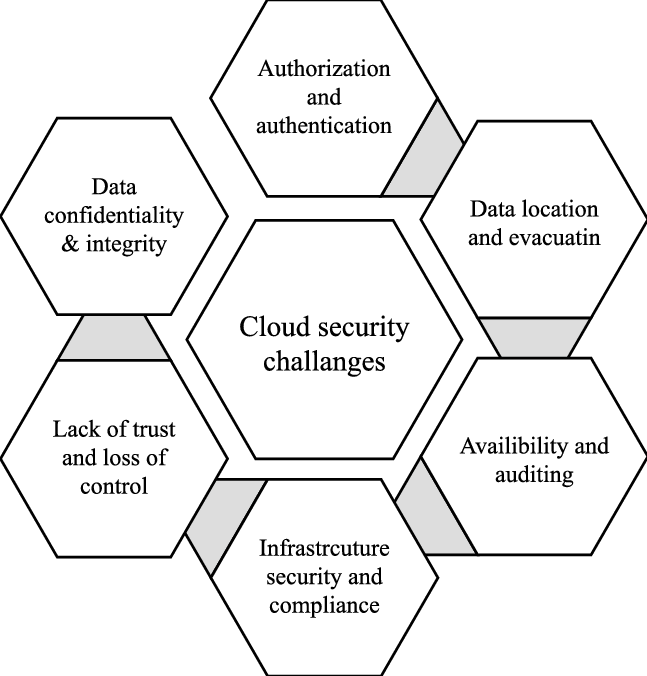
Challenges in Cloud Security
Data Breaches
Data breaches are a major concern for organizations using cloud-based software, as they can lead to the exposure of sensitive information such as customer data, financial records, and intellectual property.
Compliance Issues
Ensuring compliance with regulatory requirements is challenging in the cloud environment, where data may be stored and processed across multiple jurisdictions with differing regulations.
Lack of Control
Organizations often face challenges maintaining visibility and control over their data and applications when they are hosted on third-party cloud platforms.
Regulatory Framework in India
India has implemented several regulations and standards aimed at ensuring the security and privacy of data stored and processed in the cloud. These include the Personal Data Protection Bill and compliance standards such as ISO 27001.

Risks Associated with Cloud-based Software in India
Cybersecurity Threats
India has witnessed a surge in cybersecurity threats targeting cloud-based infrastructure, including ransomware attacks, phishing attempts, and insider threats.
Data Sovereignty Concerns
The issue of data sovereignty, or the legal jurisdiction over data, is a significant concern for Indian organizations using cloud services hosted by foreign providers.
Vendor Lock-in
Vendor lock-in occurs when organizations become dependent on a single cloud provider for their infrastructure, making it difficult to migrate to alternative solutions.
Case Studies of High-Risk Scenarios
Recent incidents in India, such as the data breach at a leading e-commerce platform and the cyberattack on a major financial institution, highlight the real-world consequences of high-risk cloud-based software.
Risk Mitigation Strategies

Encryption and Data Masking
Implementing encryption and data masking techniques can help protect sensitive data from unauthorized access.
Continuous Monitoring and Audits
Regular monitoring and audits of cloud infrastructure can help detect and mitigate security vulnerabilities and compliance gaps.
Vendor Management
Effective vendor management practices, including due diligence and contractual agreements, are essential for mitigating the risks associated with third-party cloud providers[1].
The Role of Service Providers
Cloud service providers play a crucial role in helping organizations mitigate the risks associated[2] with cloud-based software. Many providers offer robust security offerings, including encryption, threat detection, and access controls.
Benefits vs. Risks
While the benefits of cloud-based software are undeniable, organizations must carefully weigh them against the associated risks. Factors such as the sensitivity of the data, regulatory requirements, and budget constraints should be considered when evaluating cloud solutions[3].

Best Practices for Adopting Cloud-based Software
Risk Assessment Before Adoption
Conducting a thorough risk assessment before adopting cloud-based[4] software can help identify potential security and compliance issues.
Employee Training and Awareness
Educating employees about cybersecurity best practices and the importance of data protection is essential for minimizing the risk [5] of human error.
Regular Security Updates
Staying up-to-date with security patches and updates is critical for addressing newly discovered vulnerabilities and mitigating emerging threats.
Future Trends in Cloud Security
Advancements in encryption technologies, the widespread adoption of AI-driven security solutions, and increased collaboration between industry stakeholders are expected to shape the future of cloud security in India.
Conclusion
In conclusion, the adoption of cloud-based software offers numerous benefits for businesses in India, but it also presents significant security and compliance challenges. By implementing robust risk management strategies, leveraging the expertise of cloud service providers, and staying vigilant against emerging threats, organizations can mitigate the risks associated with high-risk cloud-based software and reap the rewards of digital transformation.
FAQs
- What are the most common cybersecurity threats targeting cloud-based software in India?
- How can organizations ensure compliance with data protection laws when using cloud services?
- What steps can organizations take to mitigate the risks of vendor lock-in?
- What are some best practices for securing sensitive data in the cloud?
- How do advancements in encryption technology contribute to cloud security?

